REDCap General Updates
Current Updates
Two-Factor Authentication (2FA) Update
CHR has made the decision to require two-factor authentication for logging into REDCap. Two-factor authentication will be required starting on 8/17/2020.
What is two-factor authentication (2FA)?
Two-factor authentication is an extra layer of security used to make sure that people trying to gain access to an online account are who they say they are. You may already be using 2FA to access other online systems like banking or social media sites. When you enter only your username and one password to access an account, that is considered a single-factor authentication. We are adding a second factor, or piece of information required to complete the login process, to make your account more secure.
Why are we making this change?
The use of 2FA has increased in recent years as a way of enhancing security, especially in systems that contain sensitive data. Many Kaiser Permanente systems already require two-factor authentication to log in. The second layer in two-factor authentication means a hacker or other nefarious individual would need to steal your password along with your phone to access your account. Our goal is to make our systems more secure and protect the sensitive data of our members and participants.
Who will it impact?
All users who currently log into the CHR instance of REDCap with a username and password will be impacted. This change will not impact people who are using links to complete surveys. These people are still considered participants and are not using REDCap accounts to access the system.
How will it work?
Starting Monday, August 17th, you will still enter your username and password as the first step to logging into the system. After successfully entering your username and password, you will be prompted to select one of two options for the second layer of authentication. You can choose to have a code emailed to you that will be entered into the REDCap login screen. Or you can download and set up the Google Authenticator app that will generate a login code on your smart phone. The app can be set up ahead of time so you are prepared to immediately use two-factor authentication on 8/17/2020.
Instructions on how to set up and use the two options for authentication are here.
SYSTEM UPGRADES
Current DMZ upgrades are scheduled to take place on the 3rd Sunday of each month. Internal & External REDCap upgrades will cease as we are in the process of migrating all projects to the DMZ server. Please contact Project_REDCap@kp.org with any questions.
Previous Updates
DMZ-BASED REDCAP HAS ARRIVED TO THE IHR!
In August 2019 the long-awaited DMZ REDCap instance, housed at CHR, went live for the IHR. From August 2019-November 2019 the IHR underwent a migration of all “internally-based” projects to the new DMZ instance of REDCap and the internal instance of REDCap has been officially retired. All new REDCap projects are now being built on the DMZ instance of REDCap. CHR has been an excellent partner in this transition and continues to support our work by providing oversight and routine updates to our DMZ REDCap instance. Starting in 2020, we will begin migration of “externally-based” REDCap projects, on an instance currently hosted by HostWorks, over to the DMZ REDCap instance. By tehe end of 2020 we hope to have all IHR REDCap projects migrated over and begin a path forward with a single, well-maintained instance of REDCap.
While the migration has not been without its challenges, this DMZ instance has brought with it many benefits to our work in REDCap including updates features, a single, secure location for projects, routine updates, increased oversight, and improved security. Please see below for additional details surrounding our new DMZ instance of REDCap.
DMZ REDCap Access Flow Overview
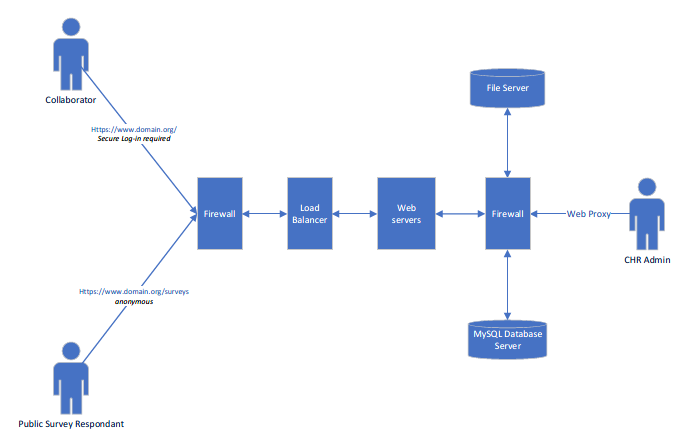
DMZ Specs
The IHR DMZ instance of REDCap is housed on a secure server hosted by the Kaiser Permanente Center for Health Research (CHR) located in Oregon. Below is some information directly from CHR on their Security, Logging, and Monitoring Systems of the DMZ REDCap.
DMZ Security
- Server room access is restricted to specific IT personnel only and is controlled via key-card access. Access is monitored and recorded 24-7.
- All server data is encrypted at rest (FIPS 140-2 compliant)
- Web, database, and file servers used to host REDCapare configured on separate virtual instances for increased fault tolerance and security
- Standard server maintenance is done on a monthly basis to ensure the latest server patches are applied
- Server backups occur nightly
- External facing web servers are tested monthly by an external firm for the latest software versions and intrusion/threat vulnerability.
- Disaster recovery includes a 2-week plan to return to operations via the last successful backup
- Only restricted internal IP address ranges are allowed for REDCapAPI requests
- Cylance Antivirus protection is applied to all servers.
- Splunk log monitoring is applied to all servers for additional security
- REDCap version releases are monitored weekly for security and bug fixes. The updates are assessed using a standard set of functional application tests and then applied to the production environment. Production updates are made on a monthly basis unless the security risk requires an immediate update.
- Data access within REDCap is limited to assigned project only. Access can be further restricted to specific record groups or de-identified data only.
- Project changes must be approved by administrator accounts before applied to the production instance
- Users are automatically logged out of the application after 15 minutes of inactivity.
- User accounts are automatically suspended after 90 days of inactivity.
- REDCap maintains an internal audit trail of all user activity and data changes.
- SSL encryption is used for all browser transactions.
- All user account requests are documented and approved by designated study staff prior to creation
- All user accounts are reviewed annually for appropriate access